Salesloft Drift Data Breach 2025
Table of Content
A recent, sophisticated supply chain attack on Salesloft Drift compromised over 700 organisations, serving as a grim benchmark for SaaS security failures. This was not a simple data breach but a calculated multi-stage attack that exploited the trusted connections between a third-party application and its customers' core platforms, like Salesforce and Google Workspace.
The breach occurred because attackers targeted a single point of failure: poorly managed OAuth tokens (see the OAuth 2.0 standard: IETF RFC 6749). These "invisible keys" granted them persistent, passwordless access to customer data across the entire Drift ecosystem. This doesn't have to be your story.
In this blog, we'll cover:
- A forensic breakdown of the Salesloft Drift attack chain and why OAuth token abuse is a game-changer.
- Actionable steps to secure your data and shield your business from third-party vulnerabilities.
- How to build a resilient defence that extends beyond your own perimeter.
Let's dive into how to fortify your business in today's interconnected digital landscape.
What Happened with the Salesloft Drift Breach? A Forensic Look
In August 2025, Salesloft Drift was compromised, impacting giants like Cloudflare, Palo Alto Networks, and Zscaler. This breach exposed far more than contact information; its primary objective was abusing OAuth/refresh tokens and extracting CRM data; some orgs also rotated exposed API tokens found in support records.
The breach unfolded in three critical stages, highlighting a severe gap in continuous monitoring and vendor risk management:
Step 1: Initial Beachhead (March–June 2025)
Attackers infiltrated Salesloft's GitHub account, downloaded sensitive repositories, and established a persistent, hidden presence by creating a guest user. This extended dwell time allowed them to map the internal landscape undetected.
Step 2: The Pivot to the Crown Jewels (June–August 2025)
The attackers laterally moved from GitHub to Drift's AWS environment. Their target wasn't customer data yet—it was the OAuth tokens. The theft of these tokens was the master key, granting them trusted, bypass-level access to connected customer platforms without needing passwords or MFA.
Step 3: Silent Data Exfiltration (August 8–18, 2025)
Over ten days, the attackers operated with impunity. Using stolen tokens, they executed systematic, bulk data queries from hundreds of Salesforce instances (see SOQL reference: Salesforce Developer Docs). Their activity appeared as legitimate traffic from a trusted application, evading traditional security controls that focus on user identity, not application behaviour.
At-a-glance: Salesloft Drift Incident
- When: Initial access Mar–Jun 2025; exfil Aug 8–18, 2025.
- How: Stolen OAuth/refresh tokens; bulk SOQL against Salesforce; a small number of Drift-Email Workspace accounts accessed.
- Who: Hundreds affected (≈700+), disclosures include Cloudflare, Palo Alto Networks, Zscaler.
- Do now: Revoke/rotate Drift tokens; audit Connected Apps (Salesforce Connected Apps); enforce phishing-resistant MFA (NIST SP 800-63B); monitor API anomalies (Google Admin: OAuth app access controls).
Impact and The Real-World Fallout
Sensitive Data & Credential Exposure: Business credentials, internal API keys, and support case data were exfiltrated, creating a downstream risk of further targeted attacks.
Cascading Service Disruption: Companies revoked the Drift integration, rotated credentials, and reviewed Salesforce/Workspace access to contain risk.
Erosion of Trust: The incident shattered the foundational trust businesses place in their vendors, proving that your security is only as strong as your weakest integrated partner.
The Salesloft Drift breach isn't just about one company's failure; it's a wake-up call for every business that uses third-party platforms to handle sensitive data. If a trusted platform like Drift can be compromised, what about the others you rely on? This breach shows how hackers can exploit weak links in the supply chain to access critical data. If it can happen to big players like Cloudflare, Palo Alto Networks, and Zscaler, it could happen to you, too.
As a business owner or decision-maker, it's crucial to ask:
- How does my vendor manage their internal credentials and OAuth tokens?
- What is my plan if a trusted vendor's security fails?
- How do I monitor for anomalous activity originating from a "trusted" application?
The Growing Risk of SaaS Supply Chain Attacks
A SaaS supply chain attack occurs when hackers bypass your defences by targeting a vulnerable third-party vendor with access to your systems. Think of it not as a burglar breaking your door down, but as one who copies your neighbour's key and walks through your unlocked connecting door.
Every additional tool in your stack—for marketing, support, or sales—expands your attack surface. When a service like Drift is compromised, the breach doesn't stop at their door; it ripples directly into your core environments.
What This Means for You: The New Reality
The Drift breach demonstrates that no vendor is inherently immune. Sophisticated attackers are now focusing on the SaaS supply chain because it offers the highest return on investment: breaching one vendor can compromise hundreds of companies.
How to Protect Your Business: Actionable Steps Beyond the Basics
Move beyond generic advice. Here is an actionable protocol based on the failures in this attack:
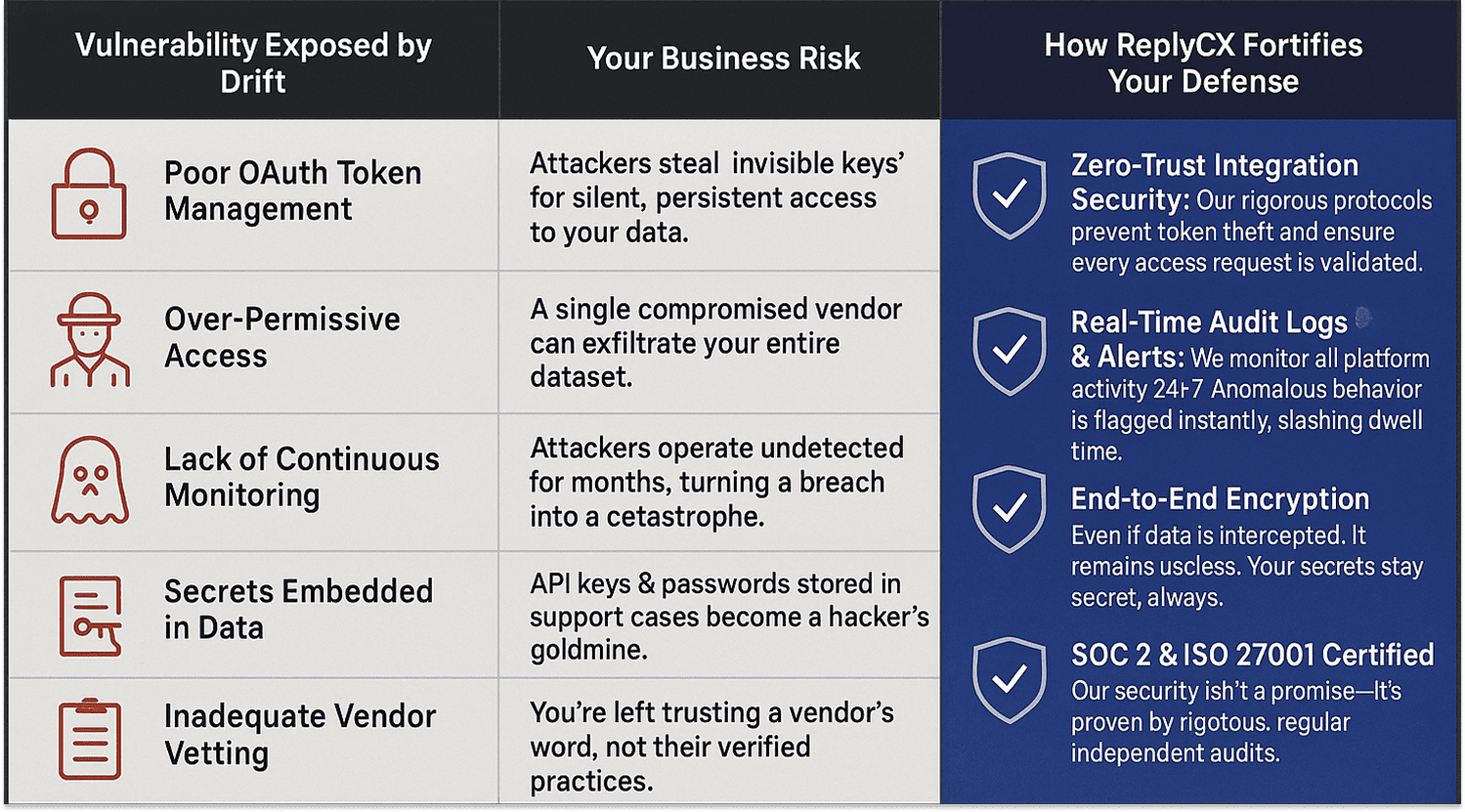
Enforce the Principle of Least Privilege (PoLP): Audit every SaaS integration. Grant only the minimum permissions necessary for it to function. Over-permissive access is what turned this breach from an incident into a catastrophe.
Demand Transparency, Not Promises: Require vendors to provide third-party audit reports (SOC 2 Type 2, ISO 27001) and disclose their subprocessor list. Scrutinise their internal security practices, not just their product features.
Implement Continuous Monitoring for Anomalous Activity: Your security tools must monitor for unusual behaviour, like bulk API queries or data downloads from a trusted application, not just block malicious IPs
How Reply.CX Architecturally Prevents a Drift-Style Breach
At Reply.CX, we've built our platform with the lessons of these exact failures in mind. Our security isn't a feature list; it's a direct response to modern attack vectors. (Learn more on our Security page.)
Defence Against OAuth & Credential Abuse:
All customer data is protected with AES 256-bit encryption, both in transit and at rest. We also limit scopes, shorten token lifetimes, and apply field-level protections to reduce the blast radius of any token misuse.
Vendor Trust Validated by Rigorous Audits:
Our SOC 2 Type 2 and ISO 27001 certifications are earned through regular, rigorous third-party audits. We prove our security controls work, so you don't have to operate on blind faith in our internal practices.
Proactive Threat Hunting, Not Passive Defence:
We employ continuous monitoring and regular penetration testing by independent experts. This means we actively hunt for vulnerabilities and simulate real-world attacks to find and fix gaps before they can be exploited, drastically reducing potential dwell time.
Transparent Governance and Control:
Full GDPR & CCPA compliance means you retain ultimate control over your data. Our commitment to transparency means our subprocessor list is available, and enterprise customers can review audit summaries to see exactly how their data is protected.
Your Future Starts with a Conversation.
- 30-minute commitment-free call
- Live product demo so you can see how AI customer service helps your business grow
- Discover how we can customize ReplyCX for your industry and business needs
Why Trust Reply.CX With Your Data?
Proven, Audited Security Track Record:
We don't just talk about security; we prove it. Our SOC 2 Type 2 and ISO 27001 certifications are independent validations that our platform meets the highest standards for data security and privacy.
Security Engineered from the Ground Up:
From end-to-end encryption to continuous monitoring, security is not an add-on but the core of our architecture. We use AES 256-bit encryption for all data, ensuring protection whether in transit or at rest.
Full Compliance with Global Standards:
We navigate the complex landscape of data privacy so you don't have to. Reply.CX is fully compliant with GDPR and CCPA, ensuring your data is handled responsibly and you have full control over your data rights.
Proactive, Not Reactive, Risk Management:
Security is an ongoing process. Our continuous monitoring and regular penetration testing identify and fix vulnerabilities before they can be exploited, ensuring we stay ahead of potential threats.
Unwavering Transparency:
We believe you have a right to know. We provide clear insights into our security practices, and our subprocessor list is available upon request. We only work with vetted partners who meet our high standards.
24/7 Vigilance and Response:
Even with the best defences, preparedness is key. Our 24/7 customer support and comprehensive incident response plan ensure we can swiftly address any concern and minimise impact, protecting your operations.

Yash Shah
Yash Shah is a tech-savvy Growth Marketing Specialist (ReplyCX), skilled in accelerating business growth, performance marketing, and SaaS SEO. Certified in Growth Hacking and backed by 6,300+ LinkedIn followers, he combines strategic sales development with operational execution to build scalable results.